|
CMPUT
300 - Winter 2012 Computers
and Society
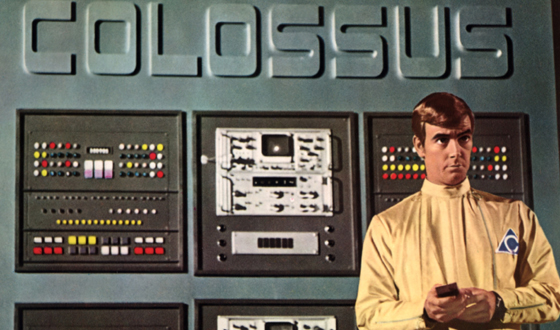
Colossus: The Forbin
Project
(produced in 1969 though released in 1970) is an American science fiction
thriller film. It is based upon the 1966 novel Colossus, by Dennis Feltham
Jones, about a massive American defence computer named Colossus becoming
sentient and deciding to assume world control. See Internet
Archive Version |
|
|
The lectures and readings listed here are subject to change. January 11: Introduction o
Textbook, Chapter 1 o The power of nightmare
(Adam Curtis) January 18: Google
versus China: Ethnical Issues
o Wired Threat Level on the attacks
o Vast Spy System Loots
Computers in 103 Countries, New York Times,
March 28, 2009 January 25: Ethics I - What is ethics? o
Textbook, chapter 9 o Paul
Berg, David Baltimore, Sydney Brenner, Richard O. Roblin, and Maxine F.
Singer, Summary Statement of the
Asilomar Conference on Recombinant DNA Molecules
PNAS 72:6, June 1975. o David
L. Parnas, "Software aspects of
strategic defense systems", Comm. ACM
28:12, December 1985. o Philip
M. Boffey, Software Seen as Obstacle
in Developing 'Star Wars', New York Times,
September 16, 1986. o
Robot
Wars-Drones, robots & the future of military February 01: Ethics II - Codes of ethics o ACM Software Engineering Code of Ethics
o
SAGE/LOPSA/Usenix System
Administrators' Code of Ethics February 08: What is
Privacy? o
The Transparent Society,
David Brin, Wired Magazine 4:12, Dec. 1996. o Cyberspace Privacy: A
Primer and Proposal, Jerry Kang, Human
Rights Magazine 26:1, winter 1999. o The Right to Privacy,
Samuel Warren and Louis D. Brandeis, 4 Harvard Law Review 193 (1890) o Dr. Fun
o What's in the driver's
license bar code? o
Textbook, chapter 2 February 15: Privacy-Wiretapping and Eavesdropping
o
Katz v. United States, 389
U.S. 347 (1967). Read all five opinions. o Smith v. Maryland, 442 U.S. 735 (1979).
Wiretapping the Net",
Steven M. Bellovin, The Bridge, 20(2):21-26, Summer 2000. The Athens Affair,
Vassilis Prevelakis and Diomidis Spinellis, IEEE Spectrum, July 2007. o Security Implications of
Applying the Communications Assistance to Law Enforcement Act to Voice over
IP, Steven Bellovin, Matt Blaze, Ernest
Brickell, Clinton Brooks, Vinton Cerf, Whitfield Diffie, Susan Landau, Jon
Peterson, and John Treichler, June 2006. February 22:
Reading Week February 29: Privacy-Legal
Issues o
Ordering Pizza,
ACLU. (Note: blatant propaganda piece...) o FBI wants records kept of
Web sites visited, Declan McCullagh, CNET News, Feb 5,
2010. o Obama's Nominee for T.S.A.
Withdraws, New York Times, Jan 20, 2010. o Identifying John Doe: It
might be easier than you think, blog posting, Feb
8, 2010. o What Third Parties Know
About John Doe, blog posting, Feb 9, 2010. o The Traceability of an
Anonymous Online Comment, blog posting, Feb
10, 2010. o
Google Buzz: Privacy
nightmare, CNET blog posting, Feb 10, 2010 March 7-14: Freedom
of Speech and e-Democracy
o
Textbook, chapter 3 o
ACLU
v. Reno, 929 F. Supp.
824 (1996) o
EFF
article on Sapient v. Geller o EFF article on Online
Policy Group v. Diebold o Rulings Leave Online
Student Speech Rights Unresolved,
Wired Threat Level blog, Feb. 4, 2010. o Exploiting Linkages for
Good, blog posting, Dec 31, 2007. o Cyber Civil Rights,
Danielle Citron, 89 Boston University Law Review 61 (2009). (Related article
that isn't required reading: Law's Expressive Value in
Combating Cyber Gender Harassment,
Danielle Citron, 108 Michigan Law Review 373 (2009).) o Anonymity and traceability
in cyberspace, Richard Clayton, PhD dissertation,
University of Cambridge, November 2005, technical report UCAM-CL-TR-653 ó
read Chapter 3. o Britain, Long a Libel
Mecca, Reviews Laws, Sarah Lyall, New
York Times, 10 December 2009. o Threat to Web Freedom Seen
in Italian Google Case, Rachel Donadio, New
York Times, 24 Febuary 2010. o
Dow Jones & Company
Inc. v Gutnick [2002], HCA 56 (10 December
2002). (skim) March
21: Social Networks
o
Hackers Assault Epilepsy
Patients via Computer, Wired Magazine,
28 March 2008. o Judge Acquits Lori Drew in
Cyberbullying Case, Overrules Jury,
Wired Magazine, 2 July 2009. o Facebook Users Keep it
Real in Online Profiles, Science News,
26 February 2010 o Hey, You're Breaking Up on
Me!, Washington Post, 13 February
2007. o The Boundaries of a
Breakup, New York Times, 20 November
2009. o Israeli Raid Canceled
After Facebook Leak, Robert Mackey, New
York Times Lede Blog, 3 March 2010. o Project 'Gaydar',
Carolyn Y. Johnson, Boston Globe, 20 September 2009. o I Am Here: One Man's
Experiment With the Location-Aware Lifestyle,
Mathew Honan, Wired Magazine, 19 January 2009. o FTC Warns of Data Breaches
from P2P File Sharing, Brian Prince, eWeek,
23 February 2010. o S. 3027, P2P Cyber
Protection and Informed User Act,
111th Congress. o Facebook tosses graph
privacy into the bin, Joseph Bonneau, Light
Blue Touchpaper blog, 11 December 2009. o
What Does Facebook's
Privacy Transition Mean For You?,
ACLU. March 28: Intellectual
Property o
Filching a Good Name for
Internet Use?, New York Times, 21 March 2010 o Billions Registered,
Joshua Quittner, Wired Magazine 2:10, October 1994. o Textbook,
chapter 4 o NFL/DMCA,
Wendy Seltzer's blog o Death by DMCA,
Fred von Lohmann and Wendy Seltzer, IEEE Spectrum, June 2006 o Frequently Asked Questions about Copyright
(skim) o Math of Publishing Meets
the E-Book, New York Times, Feb 28, 2010. o Entertainment Industry Asks White House for
Vast New Internet Monitoring, Filtering, and Takedown Powers,
Lauren Weinstein's blog, 25 March 2010. o Method of exercising a cat,
Kevin T. Amiss and Martin H. Abbott, U.S. patent 5,443,036, issued Aug 22,
1995. o Business method protecting
jokes, Timothy Wace Roberts, U.S. patent
application 10/569,506, filed Aug 24, 2004. o What is a Patent?,
up to but not including the section titled "The United States Patent And
Trademark Office" o For Texas Instruments,
Calculator Hackers Don't Add Up, D. Kushner, IEEE
Spectrum 46:12, December 2009. o
Unintended Consequences:
Twelve Years under the DMCA, Electronic Frontier
Foundation, March 2010. April 4-11: Risks/Benefits
of Computers o
Textbook, chapter 8 o An Experimental Evaluation of the
Assumption of Independence in Multi-Version Programming,
John Knight and Nancy Leveson, IEEE Transactions on Software Engineering
SE-12:1, January 1986, pp. 96-109. o Analysis of faults in an
N-version software experiment, S.S. Brilliant,
J.C. Knight, and N.G. Leveson, IEEE Transactions on Software Engineering
16:2, February 1990. (optional) o The Bug Heard 'Round the
World, Jack Garman, ACM Software
Engineering Notes, October, 1981, pp. 3-10. o Vulnerabilities of network
control protocols: an example, Eric C. Rosen, ACM
SIGCOMM Computer Communication Review 11:3, July 1981. o Who Needs Hackers?,
John Schwartz, New York Times, September 12, 2007. o Technical background on AT&T's network
slowdown, January 15, 1990 o Prius software problems?
Is the Prius stopping or stalling on the Highway?,
October 13, 2005. o Going Ballistic! A hacker
tourist explores the deep recesses of fabled Air Force stronghold Cheyenne
Mountain, where the Cold War never stops.,
Phil Patton, Wired magazine 7:11, November 1999. o 20 Mishaps That Might Have
Started Accidental Nuclear War, Alan F. Phillips.
See #18 and #19. o 'I Had A Funny Feeling in
My Gut', David Hoffman, Washington Post Foreign
Service, February 10, 1999. o History's Worst Software
Bugs, Simson Garfinkel, Wired magazine,
November 2005. o 50 Plus Blue Screen of
Death Displays in Public, Hiroshi, 14 June
2009. o An
ACM Digital Library error, which I got while
working on this lecture... o Hacking the Hill,
Shane Harris, National Journal Magazine, Dec. 20, 2008. o Researchers Trace Data
Theft to Intruders in China, John Markoff and
David Barboza, New York Times, April 5, 2010. o Jan. 28, 2001: Hey, Donít
Tampa With My Privacy, Ryan Singel, Wired
Magazine, This Day In Tech: Events That Shaped the Wired World, Jan 28,
2010. o Police secretly snapping
up to 14m drivers a day, Times Online,
April 4, 2010. o Analysis of an Electronic Voting System,
Tadayoshi Kohno, Adam Stubblefield, Aviel D. Rubin, and Dan S. Wallach, Proc.
IEEE Symposium on Security and Privacy (May, 2004). o Project EVEREST Evaluation
and Validation of Election Related Equipment, Standards and Testing,
December 2007 (optional). o Top-to-Bottom Review
(optional) o Hacking Democracy,
HBO film (optional) o Anatomy of an IT disaster:
How the FBI blew it, InfoWorld,
21 March 2005 o Guest View: It's Not Too
Late to Learn, James Shore, Software
Development Times on the Web, 15 August 2005. o The FBI Trilogy Information Technology
Modernization Program - Summary, Computer Science
and Telecommunications Board, National Academies, May 2004. o
IRS trudges on with aging
computers, CNET News, 12 April 2007. Version
March 8, 2012 |